How to setup Bitlocker for a Lab Environment to allow auto-start on VMware ESXi
I have been building out my lab environment and really wanted the ability to just shutdown the lab when I want then have it come back online and running. The major need came for this when the use of User automation started to come more into play for testing and data creation. Since Bitlocker is being used on the systems, I needed to add a way to get past the password or else it would not come online.
Now VMware ESXi 6.5+ should have access to the TPM module but that is only available when you have vCenter. Currently, I am not paying for VMUG so I do not have access to vCenter so I had to come up with a new approach. Simply just adding a Floppy Drive to each virtual machine and store the Bitlocker key on the floppy image and point Bitlocker to that was a solution.
Here is how I did it, of coarse after a bunch of Googling:
To add a Floppy Drive, you will need to turn off your Virtual Machine (VM).
To make a Floppy image to be used in the virtual Floppy Drive of the VM, you can use a program called WinImage
For some reason the Create on the floppy on the VM would not let Bitlocker right to it properly so this was a good alternative and is even recommended by VMware themselves.
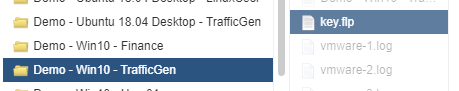
After creating the Floppy Image you can upload it multiple times to your datastore, as it is just basically a blank Floppy Disk.
Here is an image of what a Floppy Disk use to look like for all the younger readers:

You can put this right into the folder for the specific VM so it is better organized.
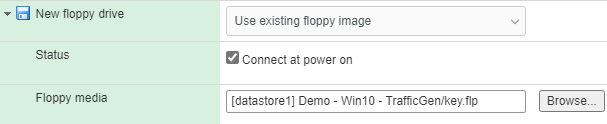
Make sure that “Connect at power on” for the Floppy Drive is enabled
You can power your VM back on and go to the BIOS, you will now need to move the Floppy Drive to the first select.
After your VM has booted up, open a Command Prompt as an administrator
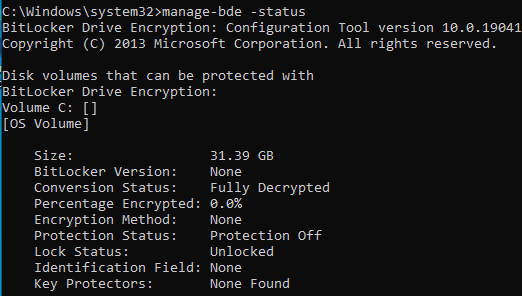
Run the command manage-bde -status to check and make sure the disk is Fully Decrypted and unlocked.
Before configuring the Bitlocker we need to set Bitlocker to allow Bitlocker without a compatible TPM. This can be done through Group Policy on a Domain Controller or you can do it through Local System Policy.
It will be located at:
Computer Configuration > Administrative Templates > Windows Compoents > Bitlocker Drive Encryption
The setting name is Require additional authentication at startup and the setting you need to ensure is enabled is Allow BitLocker without a compatible TPM
Now back to the Command prompt and run the following command:
manage-bde -protectors -add C: -startupkey A:
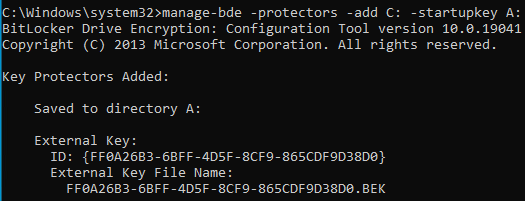
This will create the Bitlocker key for the C: drive and save it to the A: drive which should be the floppy disk
You can now run the Bitlocker command how you will like, but for now I will run this for the C drive and Used Space Only
Command: manage-bde -on -UsedSpaceOnly C: -startupkey A:
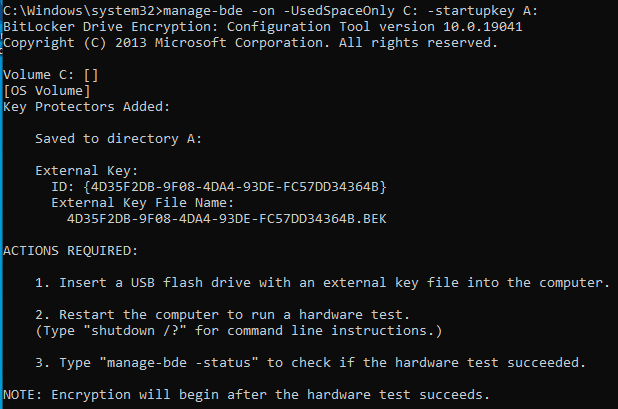
You will have to reboot the VM, but then after that it should start encrypting the Hard Drive for the VM.
Some Extra Info:
Now if you have Sophos Central Encryption, you can go ahead and add this computer to the Encryption policy for monitoring tracking and recovery purposes.